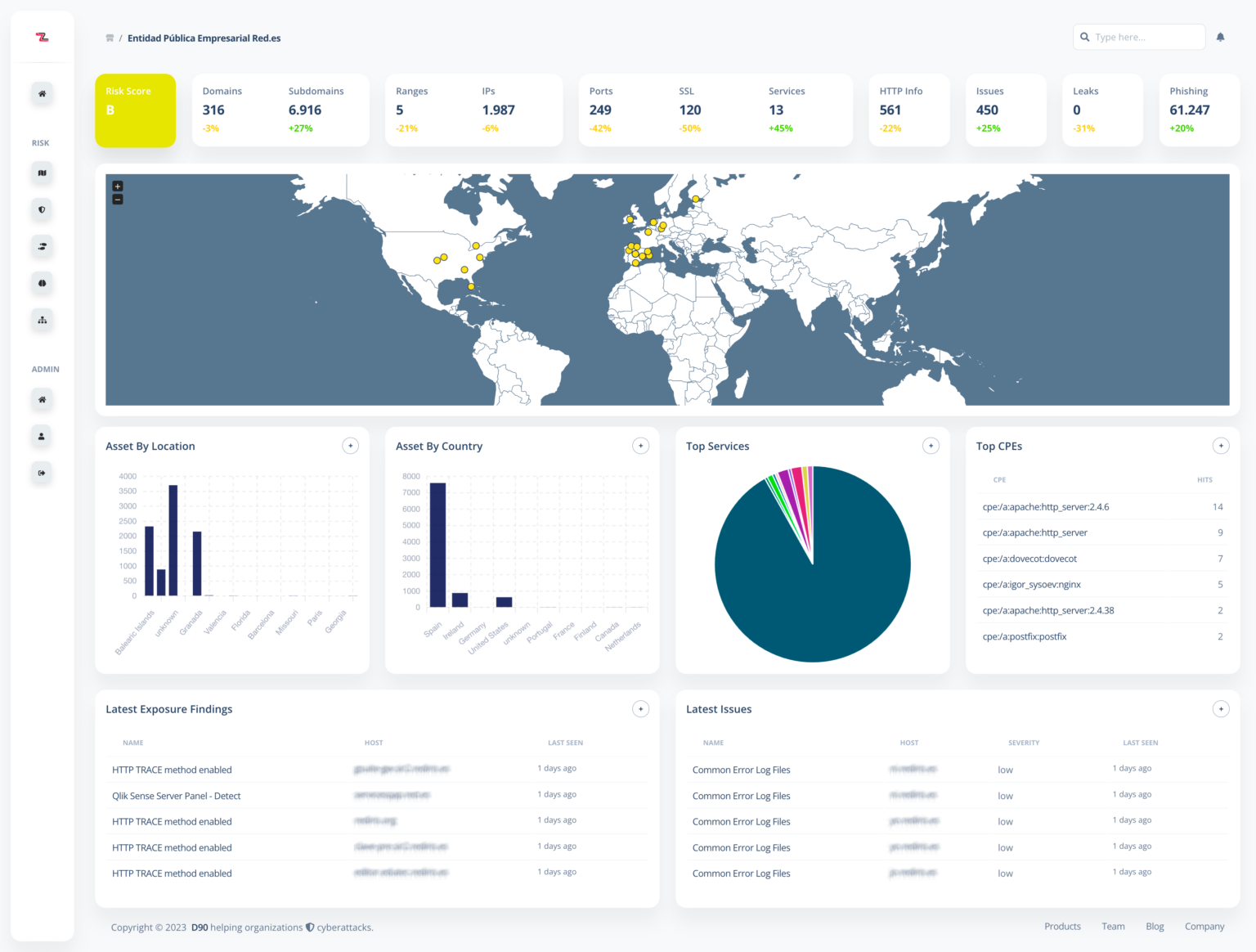
ELSA
ELSA (Local Exposure and Attack Surface) is a cyber security solution developed by DELTA90 and CCN-CERT, the Computer Emergency Response Team of the National Cryptologic Centre, CCN, under Spain’s National Intelligence Centre (CNI), and launched at XVII Jornadas STIC.
Monitoring, at a national level, of every asset connected to the Internet to detect attack vectors and exposures of any public organization or administration, improving government’s Incident Response capabilities.